MISC
最简单的misc-y1ng
下载有一个压缩包,显示有密码,直接用winrar自带的修复,可以打开里面的secret文件,以文本形式打开secret,发现有关键词IHDR,但是没有PNG,于是加上PNG头89504E47,用winhex操作,由于没有插入功能,随便打开一个文件输入十六进制字符串,然后框选住右键Edit>copy block,再到secret中,点击第一格数据,右键Edit> clipboard data>paste,再另存为png文件,就可以看到
解密就可以得到flag
有一个类似burp的在线解密(转码)网站:https://www.rapidtables.com/convert/number/ascii-hex-bin-dec-converter.html
相当好用
A_Beautiful_Picture
改文件高度,看到图片属性是1000*900,我们把高度变成1000,直接在winhex操作,点击十六进制数据直接输入就可以直接修改。先找到1000对应的十六进制数03E8,在winhex工具栏search > find hex values 可以找到03E8,跳过两个十六进制数就是高度的值,把0384改成03E8另存图片即可看到flag
EasyBaBa
真的有点小麻烦,下载后是一个jpg文件,binwalk一看有zip,foremost提取,这个zip里面有个无后缀的文件,以文本形式打开,发现有关键词avi,把后缀名改成avi,打开是我喜欢听的钉钉求饶的视频,可以看到里面快速闪过一些出题人的头像,用PR打开,一帧一帧看,然后看到有四个二维码,截图下来,用PS先调对比度,再调反色,扫描可以得到四个十六进制字符串:
424A447B696D 6167696E5F6C 6F76655F59 316E677D
拼起来就是flag BJD{imagin_love_Y1ng}
Real_EasyBaBa
画图题,winhex打开就是flag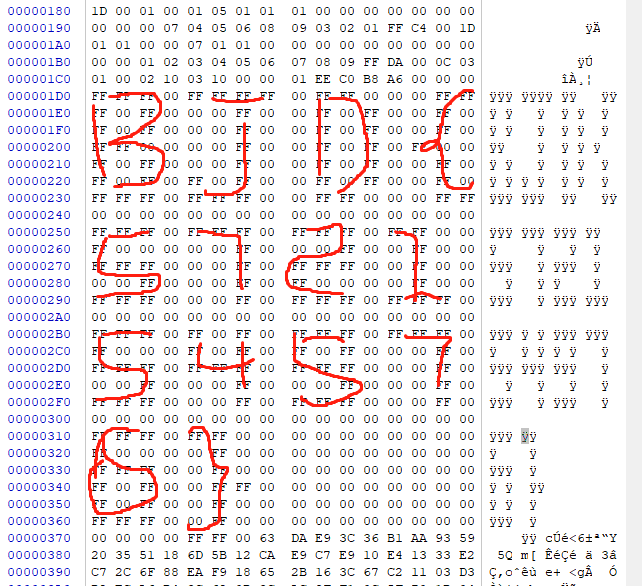
小姐姐
果然还是白学,看到图片断层,不知道就是修改图片中部数据,原来这样也可以不损坏图片,strings用了没有搜索关键词BJD简直白给,同样地也可以在winhex搜索关键词BJD,都可以找到flag,还可以strings 再 grep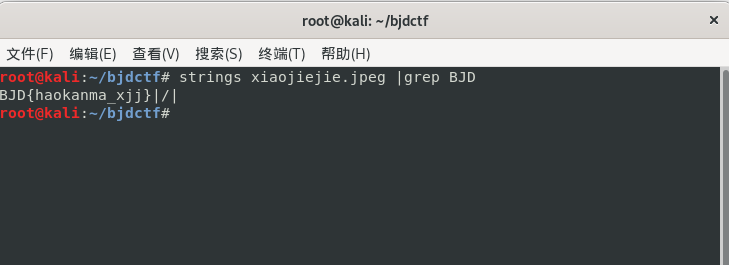
圣火昭昭-y1ng
得到的 flag 建议用 flag{} 包上提交。
开局一张图,flag全靠猜
因为出题人失误搞错了,解出来的key去掉后3位的com
下载后有一张图片,属性里有备注
新佛曰:諸壽隸僧壽降吽壽諸壽陀壽摩隸僧缽薩願心壽咤壽囉寂壽闍諸壽哆壽慧壽聞壽色吽愍壽所壽蜜如
http://hi.pcmoe.net/buddha.html
得到gemlovecom
人家猜字都加粗了,我没有想到outguess
安装outguess
git clone https://github.com/crorvick/outguess
当然一般是超慢,所以我都是上这个网站下载zip下来
然后终端中进入outguess文件夹,输入
./configure && make && make install
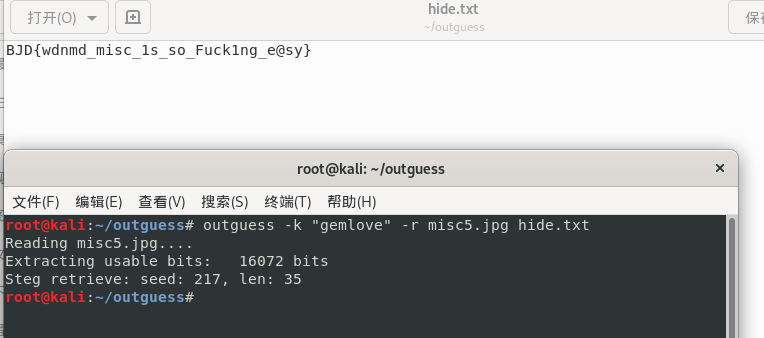
再把图片放到outguess目录下,输入
outguess -k “gemlove” -r misc5.jpg hide.txt
TARGZ-y1ng
哎? 我的tar zxvf怎么不好使了?
解压密码不需要爆破
得到的 flag 建议用 flag{} 包上提交。
压缩包的解压密码就是文件名,然后要一个一个解压,套娃题,只有写脚本了1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30import sys
import os
import zipfile
def unzip_single(src_file, dest_dir, password):
if password:
password = password.encode()
zf = zipfile.ZipFile(src_file)
try:
zf.extractall(path=dest_dir, pwd=password)
except RuntimeError as e:
print(e)
zf.close()
if __name__ == '__main__':
source_dir = r'./hW1ES89jF'
dest_dir = r'./hW1ES89jF'
password = 'OKMIlLVft'
i = 1
while True:
entry_dir = dest_dir + '/' + password + '.tar.gz'
print(i, password)
dest_dir = source_dir + '/' + password
unzip_single(entry_dir, dest_dir, password)
entry = list(os.scandir(dest_dir))[0]
if entry.is_file() and os.path.splitext(entry.name)[1] == '.gz':
password = os.path.splitext(entry.name)[0][:-4]
else:
print('error!')
print(entry)
i += 1
在解压脚本目录新建文件夹hW1ES89jF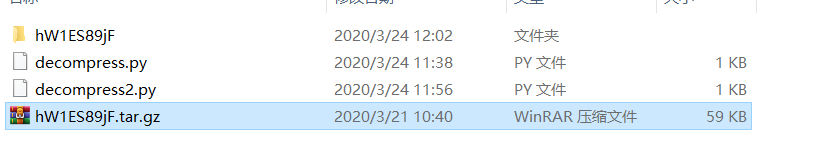
在文件夹里放解压出来的的OKMIlLVft.tar.gz
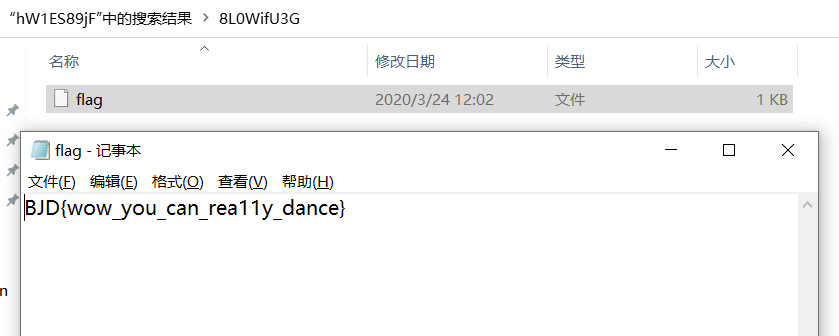
然后运行脚本,最后在文件夹内找到flag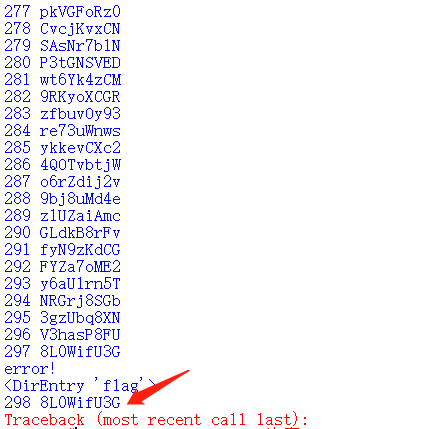
Imagin - 开场曲
在线膜听出来按键的大哥们。
CRYPTO
最全的基础加密及编码:https://www.cnblogs.com/mq0036/p/6544055.html
老文盲了
这道题真的牛皮,又多了一个梗,下载txt后内容是:
罼雧締眔擴灝淛匶襫黼瀬鎶軄鶛驕鳓哵眔鞹鰝
我一开始是一个一个查,发现头三个字首字母是BJD,那我就一个一个查,但是首字母拼起来不是flag,后面在这个网:https://zidian.911cha.com/, 把那段话放到搜索框,看到拼音。。。。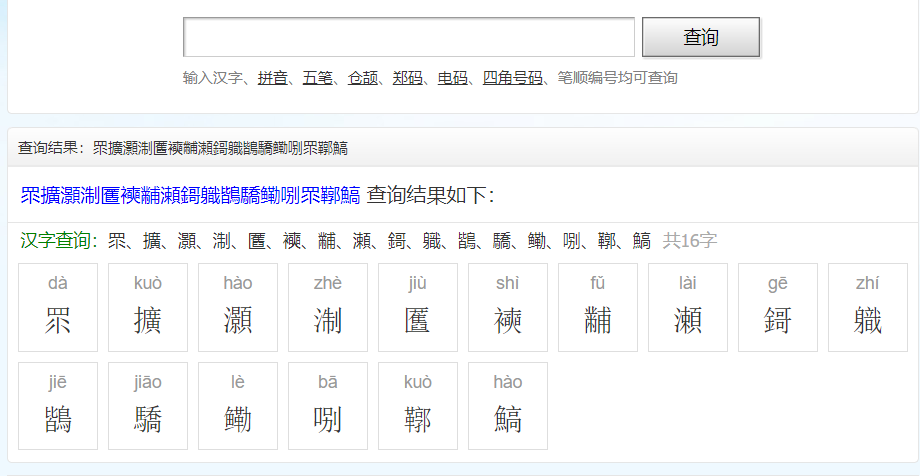
所以flag就是BJD{眔擴灝淛匶襫黼瀬鎶軄鶛驕鳓哵眔}
cat_flag
猫的gif图,刚好每行8只猫,才想到二进制数,一种颜色对应一种猫,有可能反了,反了就再反一遍,所以得到:
01000010010010100100010001111011010011010010000101100001001100000111111001111101
即BJD{M!a0~}
灵能精通-y1ng
下载后是一个jpg文件,打开后是
可以在https://www.cnblogs.com/mq0036/p/6544055.html查到是圣堂武士密码,所以再套个bjd就是flag了
BJD{IMKNIGHTSTEMPLAR}
燕言燕语
79616E7A69205A4A517B78696C7A765F6971737375686F635F73757A6A677D20
得到yanzi ZJQ{xilzv_iqssuhoc_suzjg}
所以试到了维吉尼亚密码
在线解密:https://planetcalc.com/2468/
得到bjd{yanzi_jiushige_shabi}
rsa0及rsa1
两道差不多的,都是先解出p、q,再得到n,这里用挺方便的sympy库来解
rsa0
1 | e=15005773 |
1 | import sympy |
rsa1
1 | e=11361029 |
(p-q)的平方展开可以得到p^2+q^2,然后减掉,只剩-2pq,再整除-2就是pq了,所以已知pq和p-q,用这两个方程求p和q1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22import sympy
from Crypto.Util.number import *
e=11361029
n1=228496711429634048271788696680408414851665369557196350314572825312582774948911949392882229363506632634385300189284265140583048471014043504209379692250648969390780147407942813763318085911684743305984945812956749602976720598343131062175191263000391744818763531553571798712933048013754461287572683924660757953058
n2=-6375378651571930268557772411478657497088738265045492898124718862540141136484669683309497846683249805221639669318903373169949082423999927592421461460325096
c=93060309666900524761763625930294089007166461302083918072742428303110911743262994418466259810832602768907558174079524035183493238585044278022074030362028759810008896555984430778851321141658099105629814447573069191081147109713354454920279763804024711375952839909363295106731220825173080924093408680248378245019
pq=(pow(n2,2)-n1)//(-2)
p = sympy.symbols('p')
q = sympy.symbols('q')
res = sympy.solve([p*q-pq, p-q-n2], (p, q))
print (res)#这里得到下面的p,q
p = 7014613966955691209189507850421477225368785075188184433911181920951573295307104137437017455124517603126941586059357112255107367793542351377769196310994637
q = 13389992618527621477747280261900134722457523340233677332035900783491714431791773820746515301807767408348581255378260485425056450217542278970190657771319733
n=p*q
phin = (p-1)*(q-1)
d = int(inverse(e,phin))
#d = long(inverse(e,phin)) wp脚本用python2才有的long,py3会报错,py3只有int改成int
m = pow(c,d,n)
print(long_to_bytes(m))
Y1nglish-y1ng
Welcome to our competition. Our competition is mainly for freshmen and sophomores. There are five types of topics in this competition, each of which is very basic. If you are interested in networy security, welcome to participate. Let me tell you a story. I was having dinner at a restaurant when Harry Steele came in, he is a Japanese from Japan but now he is not living in Japan, maybe Harry isn’t a Japanese name but he is really a Japanese. Harry woryed in a lawyer’s office years ago, but he is now worying at a bany. He gets a good salary, but he always borrows money from his friends and never pays it bacy. Harry saw me and came andsatat the same table. He has never borrowed money from me. While he was eating, I asyed him to lend me &2. To my surprise, he gave me the money immediately. ‘I have never borrrowed any money from you,’ Harry said,’so now you can pay for my dinner!’ Now i will give you what you want. BJD{pyth0n_Brut3_f0rc3_oR_quipquip_AI_Cr4cy}
hint说有改动,一开始不知道改哪里,尝试改AI,即使我发现里里面k和y没有正确分析出来,所以还是丢人。
正确的flag就是把y改成k:BJD{pyth0n_Brut3_f0rc3_oR_quipquip_AI_Cr4ck}
RE
RE出得像misc一样…
8086
exe文件打不开,放到ida打开,有一串诡异的字符串
]U[du~|t@{z@wj.}.~q@gjz{z@wzqW~/b;
我一开始以为不太对,想是不是加壳了,但是PEid没识别到,所以就只能从这串字符串下手,一看】和【这两个符号ascii码只差两位,而且BJD的B和J也差两位,一开始用】和B猜s1[i]=-s1[i]+233后面大括号还有另外的关系,这样得不出来全部flag,然后猜出来了,后面群里提醒才知道是异或,所以就很简单了。1
2
3
4
5
6
7
8
9
10
11s=b']U[du~|t@{z@wj.}.~q@gjz{z@wzqW~/b;'
s1=list(s)
v=[]
for i in range(len(s1)):
#s1[i]=-s1[i]+233
s1[i]=s1[i]^31
v.append(chr(s1[i]).encode('GBK','ignore').decode('GBK'))
s=''.join(v)
print (s)
#BJD{jack_de_hu1b1an_xuede_henHa0}$