MISC
ws1
跟踪http流就可以看到flag
ws2
做法有两个吧,还有我选了最弱智的不行的第三种方法
第一种
找到POST包,看到有jpeg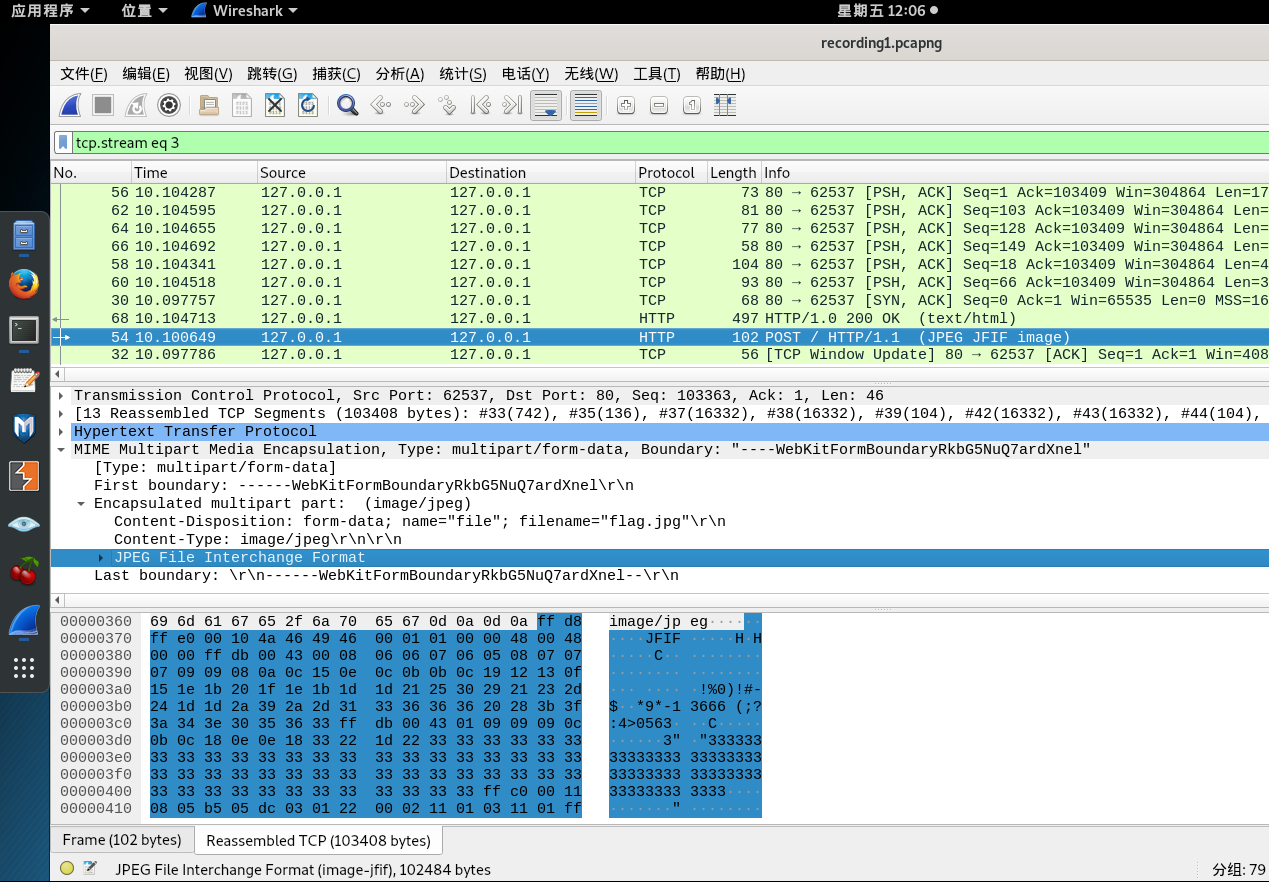
右键JPEG File Interchange Format,显示分组字节,或者导出分组字节流文件,令后缀为jpg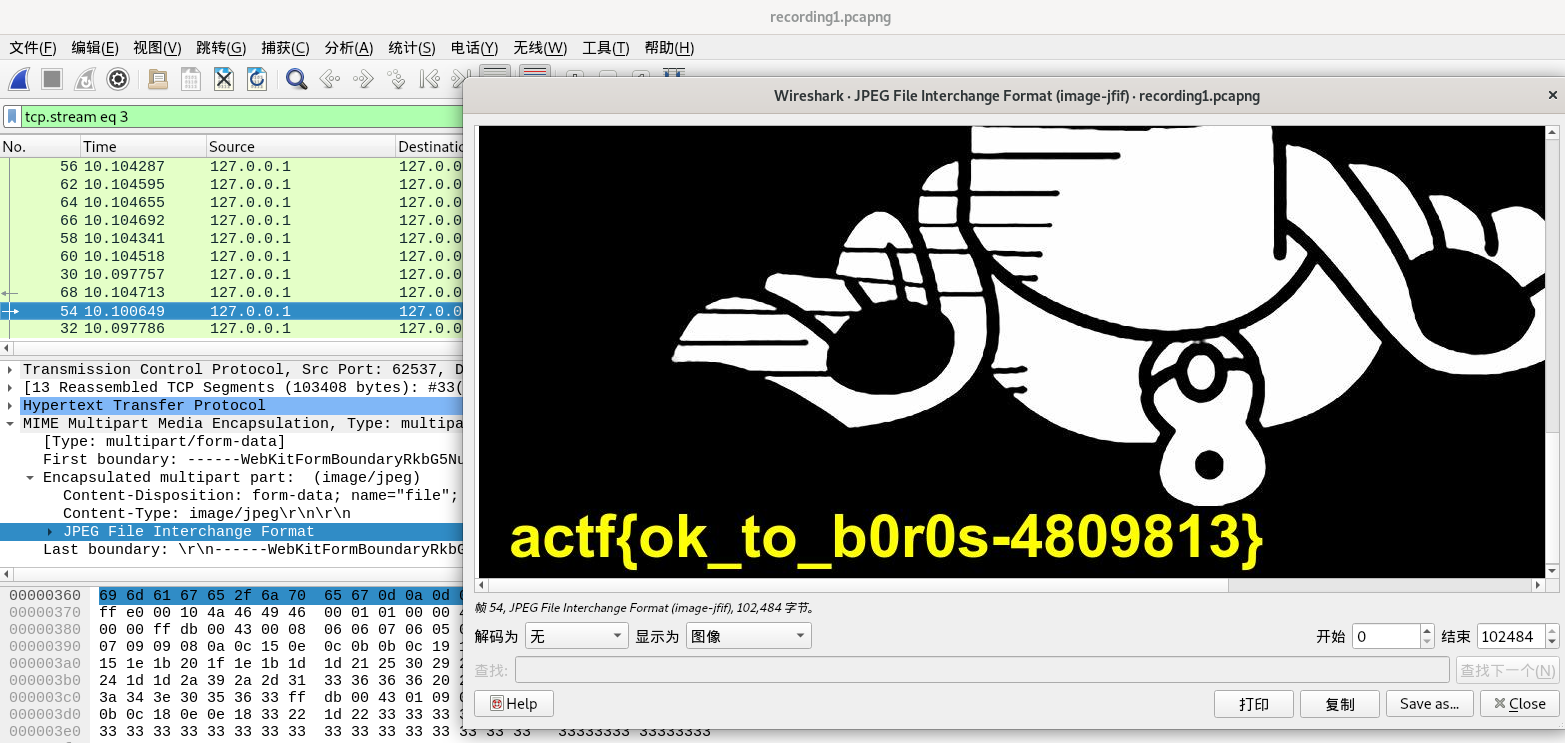
第二种
HTTP对象中有一个multipart,导出,再用foremost可以直接分离出该jpg图片
我错就错在了只会foremost这个流量包文件
ws3
做法有两个
第一种
http对象导出18kb的文件,命名为test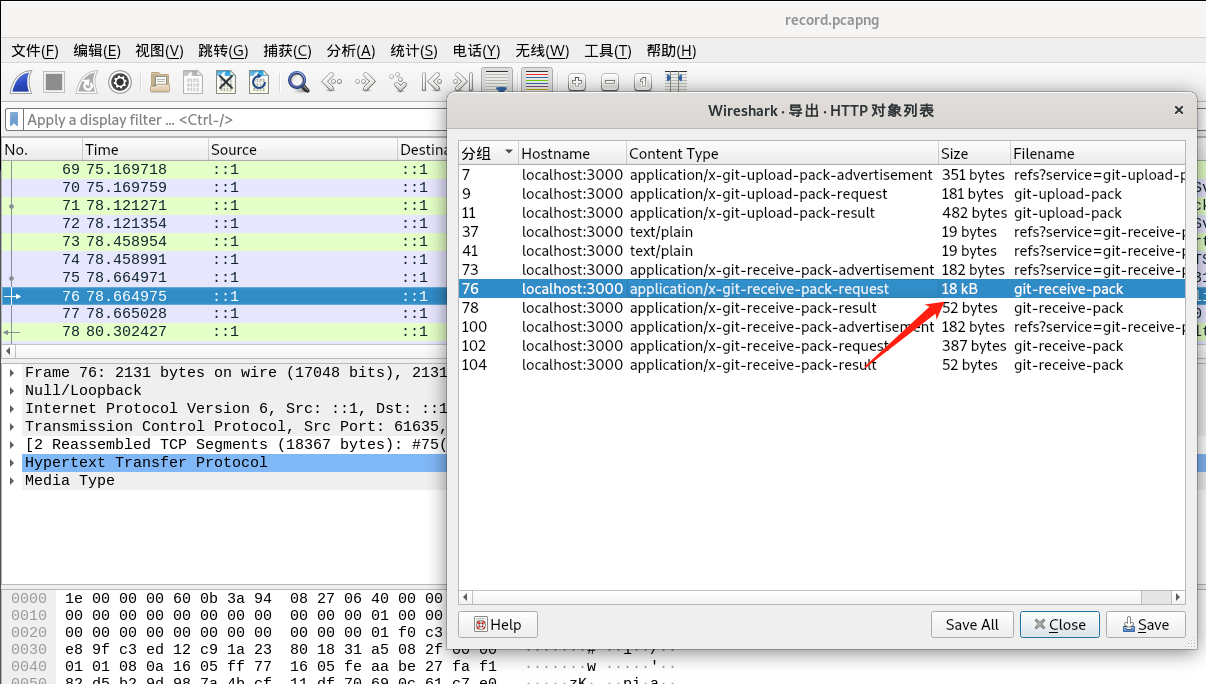
用binwalk一看只有Zlib文件,我觉得这就是为什么不能用foremost分离的原因,只能用binwalk分离,可以看到文件夹中已经提取了jpg出来了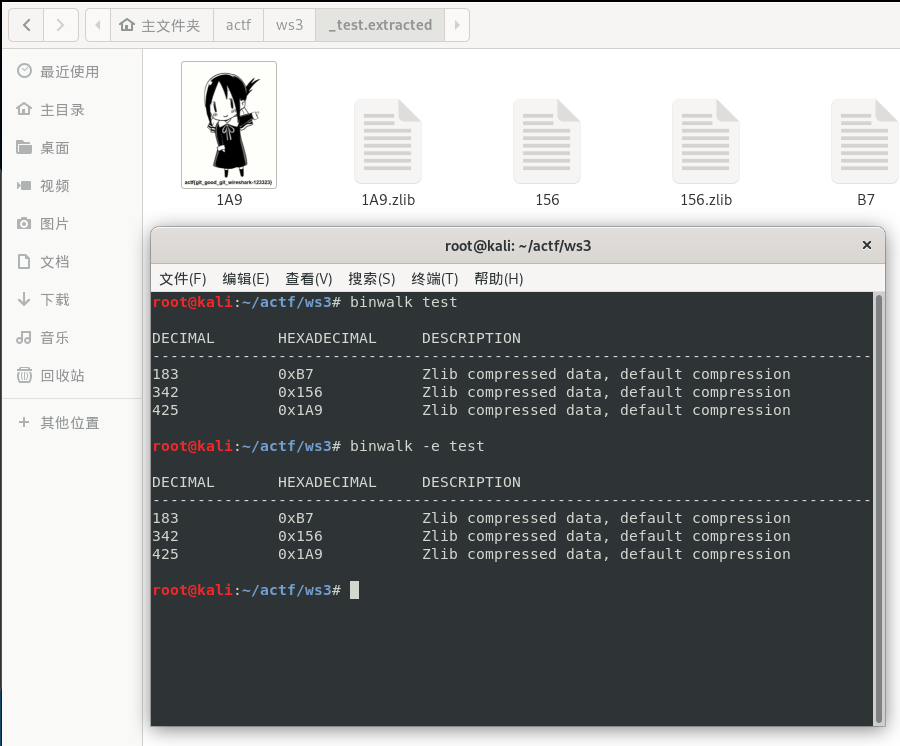
第二种
比较复杂,参考:https://github.com/joshdabosh/writeups/blob/master/AngstromCTF2020/misc/ws3.md
clam clam clam
参考:https://qiita.com/takdcloose/items/cbaed47c43d16edce402#clam-clam-clam-70pt
https://github.com/zhassan6992/angstromCTF2020-writeup/tree/master/misc/clam%20clam%20clam1
2
3
4
5from pwn import *
p = remote("misc.2020.chall.actf.co",20204)
mes = p.recvuntil(b"\x0d")
print(mes)
可以看到除了clam 还有一条消息,这是因为回车(\r)是一个控制字符。当您将其打印到终端时,终端将执行一些特殊的效果,而不是显示字形。对于回车,特殊的效果是将光标移动到当前行的开头。因此,如果打印中间包含回车的行,那么结果是下半部分被写在了上半部分之上,大概就是被覆盖的意思
nc misc.2020.chall.actf.co 20204 > output.txt
可能更为直接,然后将文本中的clam等重复字符串替换,最后只剩那句话type “clamclam” for salvation
1 | from pwn import * |
得到actf{cl4m_is_my_f4v0rite_ctfer_in_th3_w0rld}
也可以命令行敲入
echo clamclam | nc misc.2020.chall.actf.co 20204
PSK
题目中的关键词就是PSK 和 31bits
wiki这时候的突出就表现出来了,大概是因为是外国人出的题目
PSK31或“相移键控,31波特”,也叫BPSK31和QPSK31,是一种流行的计算机声卡生成的无线电传打字模式,主要用于业余无线电操作员进行实时键盘到键盘的聊天,最常使用高频业余无线电波段(近短波)的频率。是一种数字调制。
wav文件听起来就是段噪音,可以通过Fldigi 4.1.09解密,但似乎我不太能用,
下载地址:http://www.w1hkj.com/files/fldigi/
还有:https://github.com/r00tstici/writeups/blob/master/angstromCTF_2020/psk/README.md 可以参考,使用的是RX-PSK31软件
除了psk31 还有psk63
shifer
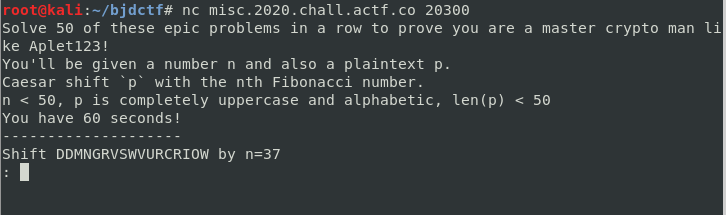
后面才看懂了题,就是n是一个序数,对应的斐波拉契数列的第n个数,也就是当n为37时,明文偏移第37个斐波拉契数,然后要在60s内算完50个问题,又是只能写脚本。1
2
CRYPTO
Keysar
带有key的凯撒加密
Hey! My friend sent me a message… He said encrypted it with the key ANGSTROMCTF.
He mumbled what cipher he used, but I think I have a clue.
Gotta go though, I have history homework!!
agqr{yue_stdcgciup_padas}
Author: joshdabosh
在线解密:http://rumkin.com/tools/cipher/caesar-keyed.php
又偏移又替换
Wacko Images
1 | from numpy import * |
还是关键的模运算,pixel[i] = pixel[i] * key[i] % 251
不吐槽了…
1 | from numpy import * |
Confused Streaming
知识盲区知识盲区,有缘再解决1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36from __future__ import print_function
import random,os,sys,binascii
from decimal import *
try:
input = raw_input
except:
pass
getcontext().prec = 1000
def keystream(key):
random.seed(int(os.environ["seed"]))
e = random.randint(100,1000)
while 1:
d = random.randint(1,100)
ret = Decimal('0.'+str(key ** e).split('.')[-1])
for i in range(d):
ret*=2
yield int((ret//1)%2)
e+=1
try:
a = int(input("a: "))
b = int(input("b: "))
c = int(input("c: "))
# remove those pesky imaginary numbers, rationals, zeroes, integers, big numbers, etc
if b*b < 4*a*c or a==0 or b==0 or c==0 or Decimal(b*b-4*a*c).sqrt().to_integral_value()**2==b*b-4*a*c or abs(a)>1000 or abs(b)>1000 or abs(c)>1000:
raise Exception()
key = (Decimal(b*b-4*a*c).sqrt() - Decimal(b))/Decimal(a*2)
except:
print("bad key")
else:
flag = binascii.hexlify(os.environ["flag"].encode())
flag = bin(int(flag,16))[2:].zfill(len(flag)*4)
ret = ""
k = keystream(key)
for i in flag:
ret += str(next(k)^int(i))
print(ret)
wp讲的都是输入a、b、c不满足1
if b*b < 4*a*c or a==0 or b==0 or c==0 or Decimal(b*b-4*a*c).sqrt().to_integral_value()**2==b*b-4*a*c or abs(a)>1000 or abs(b)>1000 or abs(c)>1000:
就输出flag,然后a、b、c要不满足条件,就是二元一次方程组解出无理数解的情况,随便丢一组abc进去就得到flag的二进制串,在转换一下就完成了。
所以我不知道中间的1
2
3
4
5
6
7flag = binascii.hexlify(os.environ["flag"].encode())
flag = bin(int(flag,16))[2:].zfill(len(flag)*4)
ret = ""
k = keystream(key)
for i in flag:
ret += str(next(k)^int(i))
print(ret)
在玩什么蛇皮,目前的认知是ret不会是flag的二进制形式(菜)
one time bad
1 | #server.py |
正常步骤是输入1,得到x和k,再根据otp函数逆出p,输入2再输入p得到flag
但是这里有个trick,如果我们一直都以A(一个ascii字符)去当作p,经过一段时间后没准能匹配到,所以我们就一直循环吧1
2
3
4
5
6
7
8
9
10
11
12
13
14
15from pwn import *
host="misc.2020.chall.actf.co"
port=20301
s=remote(host,port)
print(s.recv())
while 1:
s.sendline("2")
print(s.recv())
s.sendline("A")
ans=s.recv()
print(ans)
if b'actf'in ans:
exit()
s.close()