RGB数值转图片

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15from PIL import Image
import re
x=887
y=111 #对txt的行数进行整数分解,得到长宽
im=Image.new("RGB",(x,y))
file = open('ce.txt')
for i in range(0,x):
for j in range(0,y):
line=file.readline()
rgb=line.split(", ")
im.putpixel((i,j),(int(rgb[0]),int(rgb[1]),int(rgb[2])))
im.show()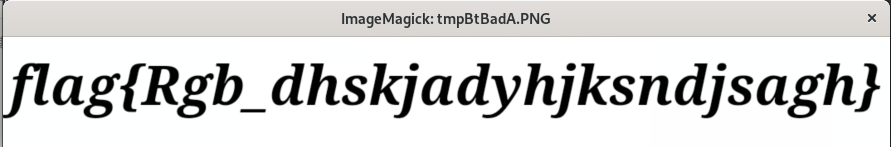
蚁剑备注
参考:https://www.fujieace.com/hacker/tools/antsword.html 下载蚁剑,修改了ua
4、user-agent修改
要注意的是,软件默认的user-agent是:User-Agent: antSword/v2.0;而且大部分人都不会去自定义useragent,这就给waf和蜜罐白白送了一个特征,所以我们要修改一下源代码:
修改项目路径:
antSword\modules\request.js (修改const USER_AGENT = ‘antSword/v2.1’; 这一行代码!)
antSword\modules\update.js (有两处要修改;可搜索“antSword/v2.0”来找到这两行代码!)
我这里是把antSword/v2.0或antSword/v2.1修改为了Baiduspider-image,我改成了百度图片蜘蛛;
Z3记录
参考:https://blog.csdn.net/s1054436218/article/details/78651075
https://zhuanlan.zhihu.com/p/30548907
用于正向线性约束求解,避免逆向分析带来的困难。
Z3 在默认情况下,只寻找满足所有条件的一组解,而不是找出所有解。
1 | from z3 import * |
DEFCAMP 2017 Misc 题 forgot my key
I forgot my flag & key. Help me recover them.
5616f5962674d26741d2810600a6c5647620c4e3d2870177f09716b2379012c342d3b584c5672195d653722443f1c39254360007010381b721c741a532b03504d2849382d375c0d6806251a2946335a67365020100f160f17640c6a05583f49645d3b557856221b2
关键函数1
2
3
4
5
6
7
8
9
10
11function my_encrypt($flag, $key) {
$key = md5($key);
$message = $flag . "|" . $key;
$encrypted = chr(rand(0, 126));#输出ascii码在0到126之间的任意一个字符
for($i=0;$i<strlen($message);$i++) {
$encrypted .= chr((ord($message[$i]) + ord($key[$i % strlen($key)]) + ord($encrypted[$i])) % 126);
}
$hexstr = unpack('h*', $encrypted);
return array_shift($hexstr);
}
因为$encrypted = chr(rand(0, 126));所以变量$encrypted首字符$encrypted[0]相当于已知$i % strlen($key)模了key的长度,所以肯定在32以内,相当于ord($key[$i % strlen($key)])即为$key[$i]$encrypted[$i]即为上一轮算出来的chr((ord($message[$i]) + ord($key[$i % strlen($key)]) + ord($encrypted[$i])) % 126)
unpack('h*', $encrypted);是把$encrypted转成十六进制字符串
如果是pack则是转换成字符array_shift($hexstr)没说是什么函数
我们的s就是array_shift($hexstr)1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43#!/usr/bin/env python3
from z3 import *
import binascii
s = '5616f5962674d26741d2810600a6c5647620c4e3d2870177f09716b2379012c342d3b584c5672195d653722443f1c39254360007010381b721c741a532b03504d2849382d375c0d6806251a2946335a67365020100f160f17640c6a05583f49645d3b557856221b2'
encrypted = []
for i in range(0, len(s), 2):
encrypted.append(binascii.unhexlify(s[i+1] + s[i])[0]) #估计这个循环是函数array_shift的逆,求出变量encrypted
print('message len:', len(encrypted)-1)
print(encrypted)
# 声明变量,encrypted 是已知,因此 IntVal 即可
encrypted = [IntVal(i) for i in encrypted]
message = [Int('flag%d' % i) for i in range(len(encrypted)-1)] #-1是因为加密函数变量encrypted有初值,比flag多一个字节
# 创建一个求解器,求解全靠它
solver = Solver()
ml = len(encrypted) - 1
# 添加明文字符的约束条件
for i in range(ml):
if i == ml - 33:
solver.add(message[i] == ord('|'))
else:
# 肯定是可见字符,因此限定范围如下
solver.add(message[i] < 127)
solver.add(message[i] >= 32)
# 添加明文和密文对照关系的约束条件
for i in range(ml):
solver.add(encrypted[i+1] == (message[i] + message[ml-32+i%32] + encrypted[i]) % 126) #模的运算级比加减号高,即m1-32+i也就是对应key[i]
if solver.check() == sat:
m = solver.model()
s = []
for i in range(ml):
s.append(m[message[i]].as_long())
print(bytes(s))
else:
print('unsat')
#message len: 103
#b'DCTF{0d940de38493d96dc6255cbb2c2ac7a2db1a7792c74859e95215caa6b57c69b2}|6941f4cac9b7784fdd77e11b51cd0d64'
whctf一道逆向
关键代码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24v1 = 0;
gets(flag);
for ( i = 0; i <= 35; ++i )
{
if ( !flag[i] )
{
flag[i] = 1;
++v1;
}
}
if ( v1 != 9 )
exit(0);
convert(a);
Transposition(a);
Multi(a, b);
for ( j = 0; j <= 5; ++j )
{
for ( k = 0; k <= 5; ++k )
{
if ( c[0][k + 6 * j] != d[0][k + 6 * j] )
exit(0);
}
}
printf("congratulations!you have gottern the flag!");
其中convert(a)是将flag赋值给a,你可以把a当做一个6*6的矩阵。
Transposition(a)是把a的转置矩阵赋值给b
Multi(a,b)是把a和b的乘积赋值给c
而d就是堆中正确的flag经过上述运算后的结果,1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65#coding:utf-8
'''
@DateTime: 2017-11-28 10:19:29
@Version: 1.0
@Author: Unname_Bao
'''
from z3 import *
import time
t1 = time.time()
#创建一个解决方案实例
solver = Solver()
#flag长度先设置为36,包括尾部的9个1
flag = [Int('flag%d'%i) for i in range(36)] #设36列1行的字符串
#保存flag的矩阵
a = [i for i in flag] #因为定义了flag,所以可以设flag为36列1行的矩阵
#保存flag的转置矩阵
b = [i for i in range(36)]
#保存a*b的矩阵
c = [0 for i in range(36)]
#堆中正确flag的运算结果
d = [0x12027,0x0F296,0x0BF0E,0x0D84C,0x91D8,0x297,
0x0F296,0x0D830,0x0A326,0x0B010,0x7627,0x230,
0x0BF0E,0x0A326,0x8FEB,0x879D,0x70C3,0x1BD,
0x0D84C,0x0B010,0x879D,0x0B00D,0x6E4F,0x1F7,
0x91D8,0x7627,0x70C3,0x6E4F,0x9BDC,0x15C,
0x297,0x230,0x1BD,0x1F7,0x15C,0x6]
#获得a的转置矩阵
for i in range(6):
for j in range(6):
b[i+6*j] = a[6*i+j]
#运算a*b
for i in range(6):
for j in range(6):
for k in range(6):
c[j+6*i] = c[j+6*i] + a[6*i+k]*b[6*k+j]
#添加约束,正确flag的运算结果
solver.add(simplify(c[j+6*i]) == d[j+6*i])
#添加约束,除了尾部,flag的字符一定在可见字符范围内
for i in range(6,36-10):
solver.add(flag[i]>=32)
solver.add(flag[i]<=127)
#添加约束,由于flag有格式,前6位一定为whctf{
for i in range(6):
solver.add(flag[i] == ord('whctf{'[i]))
#添加约束,flag的尾部为9个1
for i in range(36-9,36):
solver.add(flag[i] == 0x1)
#添加约束,flag的最后一个肯定是}
solver.add(flag[-10] == ord('}'))
#这里一定要有,不check的话会报错
if solver.check() == sat:
m = solver.model()
s = []
#获得结果
for i in range(36):
s.append(m[flag[i]].as_long())
#输出flag
print(bytes(s))
else:
print('error')
t2 = time.time()
print(t2-t1)
#D:\2017_WEB_Test\ulb_manager\backend\spider>python z3test.py
#b'whctf{Y0u_ar3_g00d_a7_m4th}\x01\x01\x01\x01\x01\x01\x01\x01\x01'
#4.042840003967285